The individual behind the $9.6 million attack on the decentralized money-lending platform zkLend earlier this year claims to have recently become a victim of a phishing site masquerading as Tornado Cash, resulting in the loss of a substantial portion of the funds they had stolen.
In a communication directed to zkLend via Etherscan on March 31, the hacker asserted they lost 2,930 Ether (ETH) from the stolen assets due to the phishing site that imitated Tornado Cash’s front-end.
During a series of transfers on March 31, the zkLend perpetrator sent 100 Ether at a time to an address labeled Tornado.Cash: Router, concluding with three additional deposits of 10 Ether each.
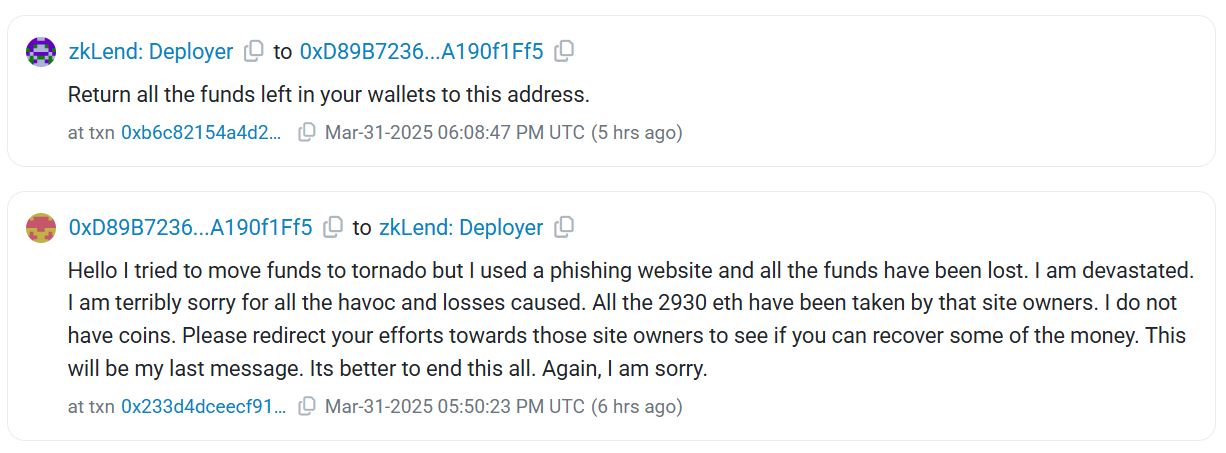
“Hello, I attempted to move funds to a Tornado, but unfortunately, I used a phishing site, and I’ve lost all the funds. I’m deeply upset. I sincerely apologize for the chaos and losses that have resulted from this,” the hacker expressed.
The hacker involved in the zkLend exploit claims that most of the funds were lost to a fraud site impersonating Tornado Cash.
“All 2,930 ETH have been taken by the owners of that site. I have no coins left. Please focus your efforts on those site owners to attempt to recover some of the funds,” they added.
zkLend responded to the hacker’s message by requesting them to “Return all the remaining funds in your wallets” to the zkLend wallet address. However, according to Etherscan data, another 25 Ether was subsequently sent to a wallet identified as Chainflip1.
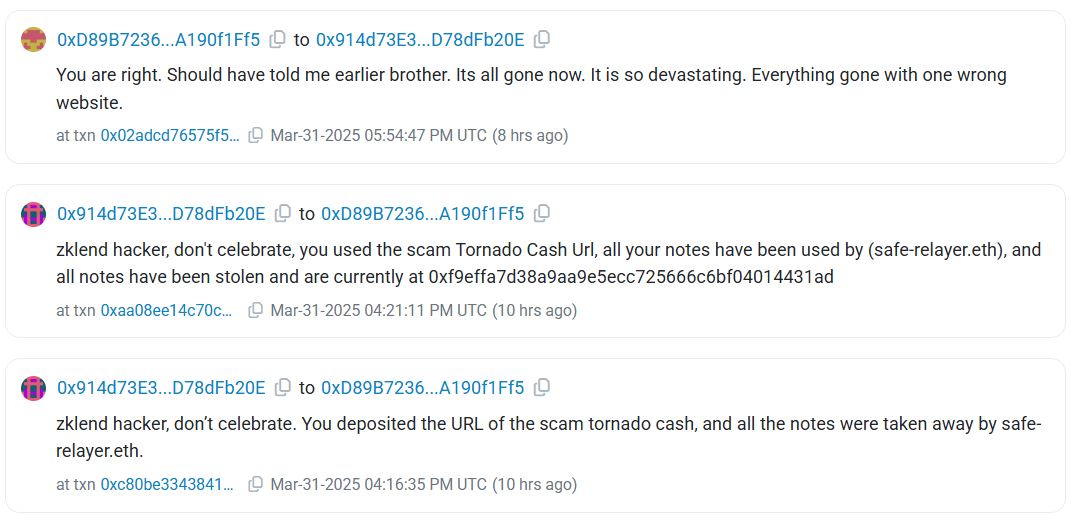
Previously, another user cautioned the exploiter about this mistake, warning them not to celebrate as all the funds had been directed to the fraudulent Tornado Cash link.
“It’s incredibly devastating. Everything has vanished because of one wrong website,” the hacker lamented.
Another user alerted the zkLend exploiter to their error, but the damage was already done.
How zkLend was exploited for $9.6 million
zkLend was hit by a market exploit on February 11, when an attacker employed a minimal deposit alongside flash loans to manipulate the lending accumulator, according to the protocol’s post-mortem released on February 14.
The hacker made numerous deposits and withdrawals, taking advantage of rounding mistakes that had amplified due to the inflated accumulator values.
After transferring the stolen assets to Ethereum, the hacker attempted to launder them through Railgun, which ultimately did not succeed as the protocol rules reverted the funds back to the original wallet.
In response to the exploit, zkLend proposed that the hacker could keep 10% of the stolen funds as a bounty, while also offering to absolve the individual from legal liability and law enforcement scrutiny if the remaining Ether was returned.
Related: DeFi protocol SIR.trading loses entire $355K TVL in ‘worst news’ possible
The deadline for this offer of February 14 passed without any response from either side. On February 19, zkLend announced it was now offering a $500,000 reward for any verifiable information that might lead to the apprehension of the hacker and the recovery of the stolen funds.
According to blockchain security firm CertiK, losses attributed to crypto scams, exploits, and hacks reached over $33 million, although this total dropped to $28 million after 1inch managed to recover its own stolen funds.
In February alone, losses from scams and attacks in the crypto sphere amounted to approximately $1.53 billion. The $1.4 billion February 21 assault on Bybit attributed to North Korea’s Lazarus Group accounted for much of this total and set a record as the largest crypto hack ever, surpassing the previous record of $650 million set by the Ronin bridge hack in March 2022.
Magazine: Lazarus Group’s favorite exploit revealed — Crypto hacks analysis
