The market share of Bybit has returned to its pre-hack levels after experiencing a $1.4 billion security breach in February. This recovery follows the exchange’s implementation of enhanced security measures and improved liquidity options for retail investors.
The cryptocurrency sector faced its largest-ever hack on February 21, resulting in Bybit losing over $1.4 billion in liquid-staked Ether (stETH), Mantle Staked ETH (mETH), and various other digital assets.
In spite of the magnitude of the breach, Bybit has consistently regained its market presence, as detailed in a report from early April by a cryptocurrency analytics agency. “Since the initial drop, Bybit has gradually regained market share as it seeks to rebuild user trust and as trading volumes return,” the analysis noted.
The report highlighted that Bybit’s market share climbed from a post-hack low of 4% to approximately 7%, indicating a robust and steady resurgence in spot market activity and trading volumes.

Bybit’s spot volume market share compared to the top 20 centralized exchanges.
The hack transpired amidst a broader trend of macro de-risking that started before the incident, suggesting that Bybit’s initial dip in trading volume was not solely due to this breach.
Related: Will Ether surpass $3,000 following Bybit’s substantial $1.4 billion hack?
The perpetrators took 10 days to launder the stolen funds through the decentralized cross-chain protocol THORChain, according to reports.

North Korean hacking activities prior to and following July 1.
Despite the recovery efforts, a staggering 89% of the stolen $1.4 billion remains traceable, as noted by blockchain analytics professionals.
Related: THORChain generates $5M in fees and $5.4B in volume post-hack.
Lazarus Group’s 2024 Pause Linked to Bybit Hack Strategy
Blockchain security firms have pointed to North Korea’s Lazarus Group as the likely assailant behind the Bybit breach, with the attackers continuing to exchange the stolen assets in a bid to obscure their trail.
There was a noticeable decrease in illicit activities associated with North Korean cyber operatives after July 1, 2024, even as attacks surged earlier in the year. These developments raised alarms, according to research lead Eric Jardine from a blockchain analytics firm.
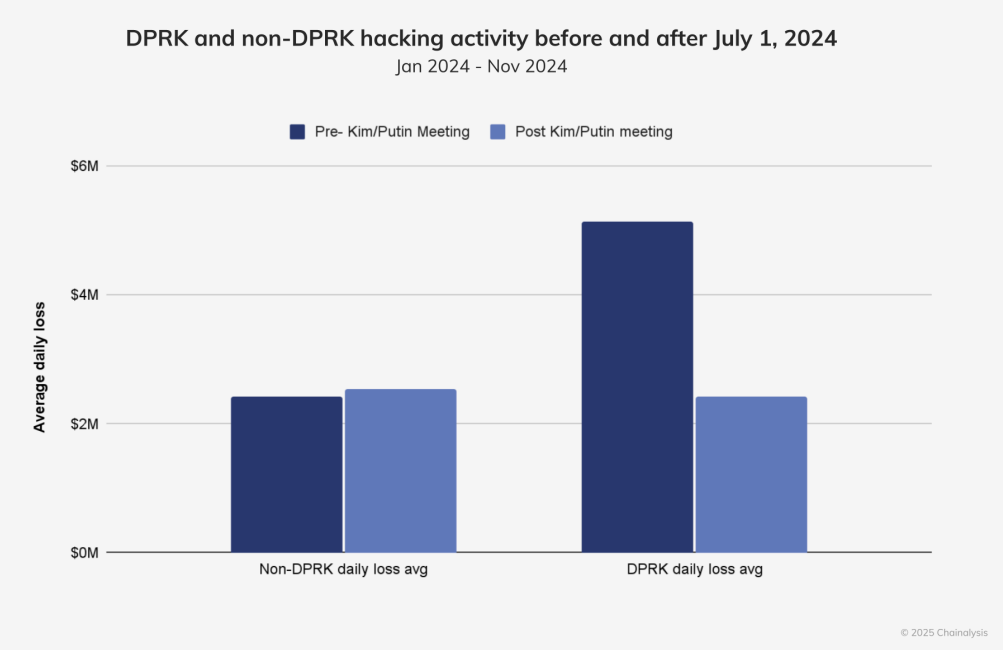
Variance in North Korean hacking activities around mid-2024.
The decline in hacking activities from North Korean operatives coincided with a meeting between Russia and North Korea, leading to a redistribution of resources, including military personnel, towards the ongoing conflict in Ukraine, Jardine explained in a recent interview.
“We speculated in the report that there might be additional, unseen reallocations of resources from North Korea, and then just a short while later, the Bybit hack happened.”
The Bybit incident underscores that even centralized exchanges equipped with strong security protocols are not immune to advanced cyber intrusions, analysts have concluded. This attack bears similarities to previous high-profile breaches, emphasizing the persistent vulnerabilities within the cryptocurrency landscape.
